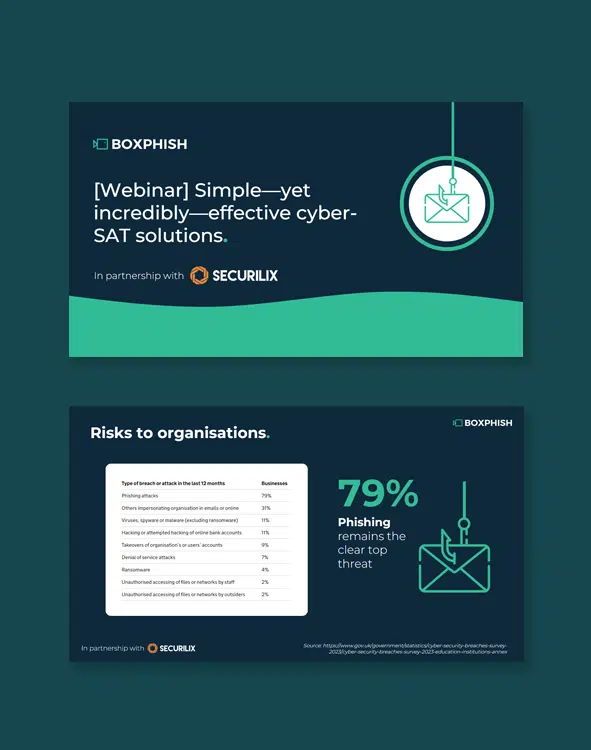
Empower your people to spot cyber-attacks
Improve your cyber security culture and educate employees with real-world phishing simulations, quality training content and actionable data.
Our customers
Trusted by thousands globally













Our product
Everything you need in a single automated platform

Phishing simulations
Our library of phishing simulations allow you to test your organisations susceptibility to attack and raise internal awareness amongst employees on the latest threats. Choose from a number of ready-made templates that mimic real-world attacks, and track the results.
Learn more

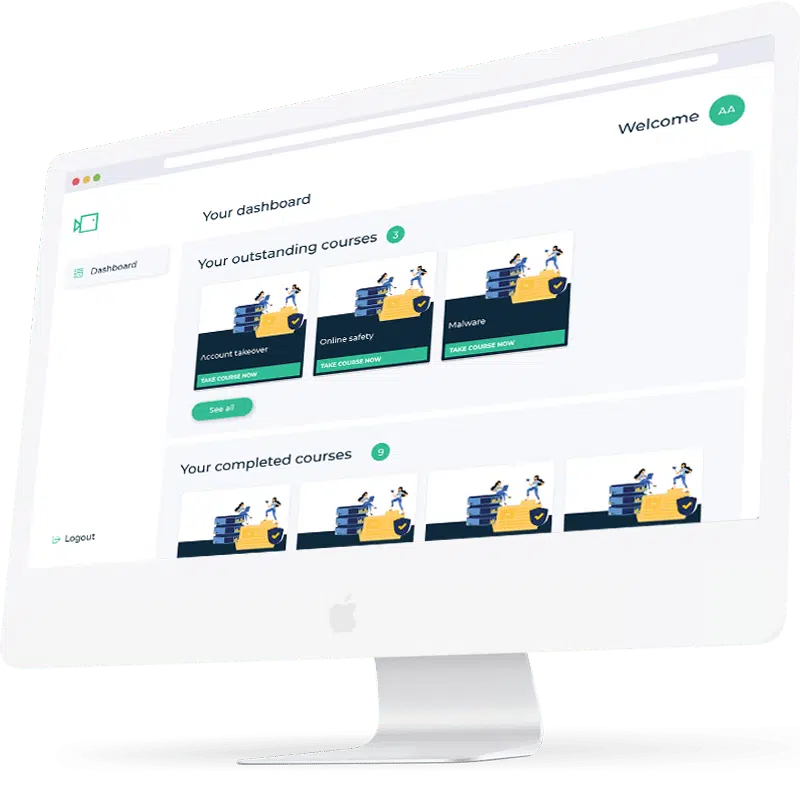
Training courses
Follow simulations with focused, relatable training content that educates your employees on best-practice cyber security advice. A mixture of short video-based learning and quizzes ensure training is delivered in a way that is engaging and maximises information retention.
Learn more

Actionable data
Use our analytics to pinpoint weak spots following a phishing simulation, track training course completion rates, and monitor your improving cyber awareness culture. Out-of-the-box dashboards are perfect for evidencing your efforts and reporting back to the board.
Learn more
Proven cyber security awareness solutions
Boxphish provide cyber security awareness training solutions that are proven to improve organisation-wide cyber awareness and reduce human error.
Recent analysis of over 400K Boxphish platform users revealed that untrained users are 8.8 times more likely to click on a phishing email than those receiving regular training.
Your people are often your first line of defence, and they are being targeted everyday by increasingly sophisticated phishing attacks. Through a combination of learning-based phishing simulations and short, regular training content you can train your employees to quickly identify and report potential attacks.
Loved by users, backed by G2.











Train your people to spot cyber-attacks.
Effective risk mitigation goes beyond technical controls. Your people are often your first line of defence. Train them to spot the latest attacks through a combination of phishing simulations and regular cyber awareness training.
%
82% of data breaches are a result of human error
Verizon
%
40% of organisations experience an attack at least once a month
Gov.uk
%
79% of cyber-attacks are phishing attacks
Gov.uk
%
100% of enterprises should report cyber risk to the board
Our product
Designed with automation and scalability in mind
Automated
The platforms low-touch nature means you can set and forget. You’ll have complete confidence that your employees are getting the training they need to protect themselves, and your organisation, without reliance or strain on internal resources.

Scalable
Everything is accessed from a single platform that has been designed with simplicity in mind. Deployment is quick and scalable, from a single organisations with 50 employees through to global enterprises with tens of thousands.

Service
With Boxphish, you don’t just get a quality product, you also benefit from an industry leading service. Our team will not only assist you with deployment, but day-to-day support queries and on-going success management.
Request a quote
Fill out the form below and a member fo the team will be in touch
Boxphish get a quote
Why choose Boxphish?
Here’s what some of our customers have to say
“The Boxphish platform has helped us raise cyber awareness across our business and build a real culture of security. We issue tailored Boxphish training content monthly to all colleagues. The videos are short, punchy and relevant for work and home life and can be completed any time on any device without impacting the day job. This regular bite size training is helpful in repeating best practice messages, helping us to protect both ourselves and our company.”
Organisational Design & Development Manager, Eurocell
“Boxphish has very quickly had a brilliant impact on the security culture at the council. The content of the educational modules and simulations are really well thought out, accessible and engaging across the whole workforce, meaning they can be used very effectively right out of the box. Implementing, running and maintaining the system requires very little administration – a huge advantage for small teams with limited resources.”
Principle Information Security Officer, North Lincolnshire Council
“The training courses delivered via the Boxphish platform have been well received by our employees and we are seeing great results. Traditional training methods can be extremely long-winded, taking hours, if not days. Being able to deliver training content frequently but with minimal effort from an administration point of view has been incredibly valuable. The content is short, snappy and to the point, and this has had a positive impact on employee engagement levels and overall completion rates.”
Information Security Advisor & Data Protection Officer, Robertson
“Boxphish offer a wide range of phishing simulations ideal for educating our staff. They’re quick to setup and send, and easy to report on. Being able to identify the weaker spots within our growing Multi Academy Trust has allowed us to be really targeted with our training and we’ve seen great results so far.”
Head of IT, NPCAT
“Working with Boxphish has enabled me to efficiently deploy an automated cyber awareness programme so I can feel confident we are doing everything we can to educate our end users on the evolving cyber threats, it has been a great experience using the platform.”