Phishing attacks are consistently on the rise, with over 3.4 billion phishing emails delivered each day. Cyber criminals are becoming more and more sophisticated, not only using spear phishing tactics, but designing their emails so meticulously that it’s almost impossible to spot a phishing email from the real thing – unless you know how.
You can find out more about how to identify phishing attacks in another of our recent blog posts, but which are the brands that should immediately be raising a red flag when they enter your inbox?
The Top Brands
Although the official ‘top spot’ for most impersonated brand is open to interpretation, it is widely agreed that there are a small group of brands that consistently make it to the podium.
Unsurprisingly they’re brands that almost everyone uses on a very regular basis, making communications from them frequent and expected. Let’s dig into a few and see if you can identify the fakes from the facts:
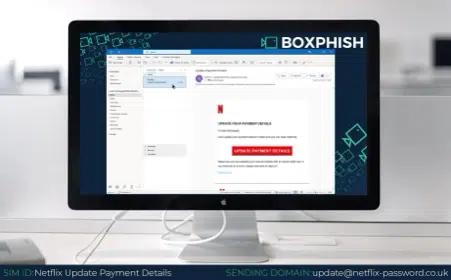
Netflix – this phishing attack prompts the recipient to update their payment details, or they risk losing access to their account. It uses a threat to try and get the victim to act impulsively, without checking whether the site address is correct, or the link is legitimate. In cases like this, hovering over the link on your desktop will often reveal the true source and through this you can quickly identify whether the email is phishing or not.
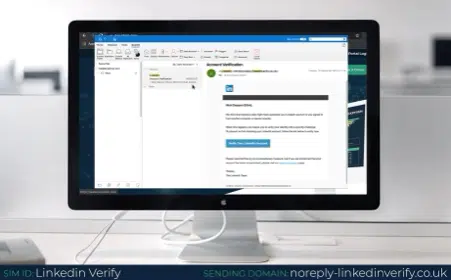
LinkedIn – vying with Microsoft, the LinkedIn phishing email is now one of the most common. Whether it’s asking the recipient to verify their account or reset their password, there has been a significant rise in LinkedIn phishing emails over the last five years. Cyber criminals like to target people on LinkedIn, because it is often an easy way of finding out professional information about them and, if they manage to hack the private social media account, it could open doors for the company accounts too. Again, you should hover over the link in these emails to determine whether it is legitimate or not, or go to your LinkedIn account from a separate device/browser to determine whether your access has truly been restricted.
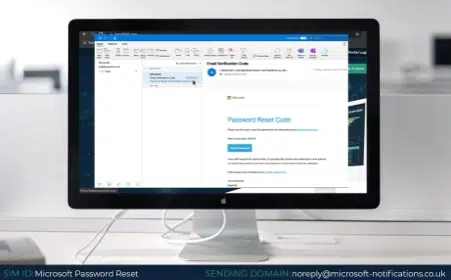
Microsoft – this has been one of the most common phishing emails for many years now, prompting users to reset their password after a suspicious login attempt. These phishing emails are very clever, as they suggest foul play has already taken place, often prompting the victim to act without thinking first. The best thing to do in this scenario is try to access your account from another device to see if the claim is real and never click on the link without inspecting the source first.
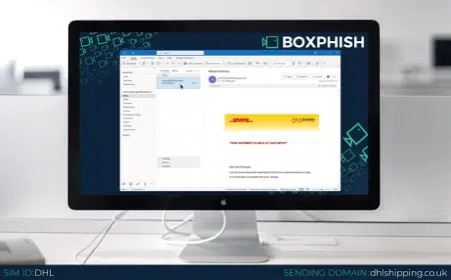
DHL – these emails operate on a chance basis that you have a delivery on the way. There are instances where cybercriminals may be monitoring your social media pages waiting for you to announce you’ve made a purchase, at which time a targeted spear phishing attack with a delivery email would have an increased chance of causing you to click. Always be careful about what you post on social media and if you receive a delivery email you’re unsure about, check for other recent communications from the same source and see if the sender address and details match before clicking on any links.
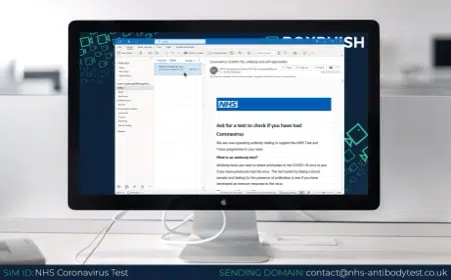
NHS – following the pandemic, phishing emails supposedly sent from the NHS have become increasingly common. These play on the recipients fears and emotions, making them extremely dangerous. Remember, the NHS will never try to contact you via email without including some personal information, like your NHS number, so be wary about how you interact with these emails.
What to watch out for
- Misspellings or missing letters in brand names & email addresses
- Requests to click on a link
- Urgent language
- Requests for bank details or a payment requests
Get in touch
If you’d like to find out more about how you can protect yourself or your organisation from phishing, Boxphish has the tools to help. At Boxphish, we are passionate about providing our users with the skills needed to identify and avoid cyber security attacks, reducing risk and protecting both the individual and the organisation.
We use interactive training and real-world attack simulations to educate and train our users, with phishing simulations delivered directly to your inbox and courses tailored to individual needs and industries. Our training is extremely easy to use and does not eat into valuable work hours for your employees. Click here to view our phishing training and book your demo today.